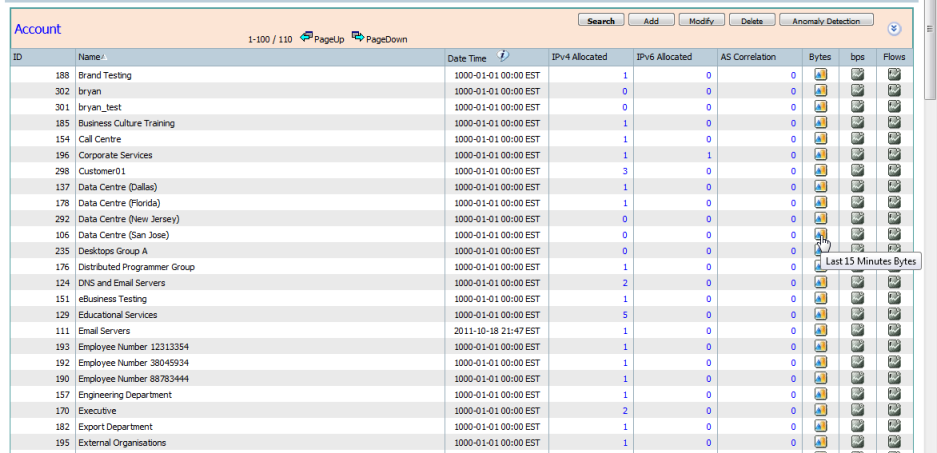
Command Overview
- Search
- Add
- Modify
- Delete
- Anomaly Detection
Command Buttons
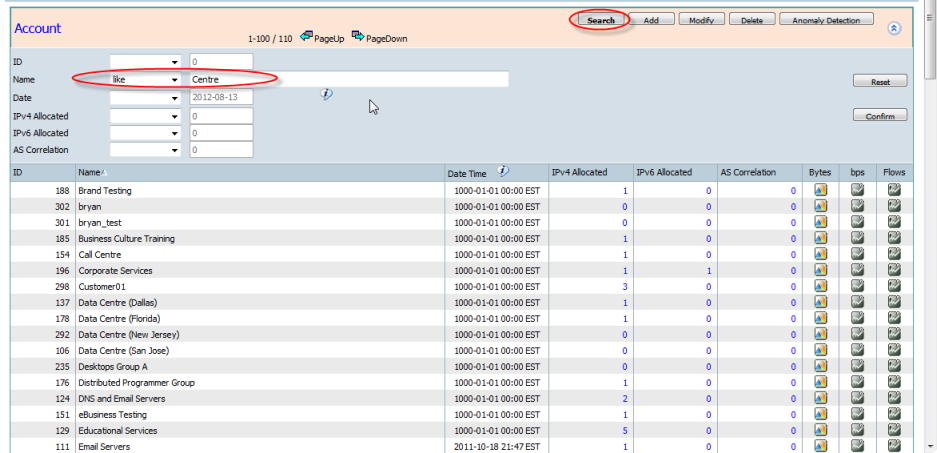
- Search - The "Search" button will expand the Search panel.
ID, Name, Date, IPv4 Allocated, IPv6 Allocated, AS Correlation can all be searched by choosing an operator and entering a value.
Pressing the "Confirm" button will list the matched Accounts.
- Add - The "Add" button will expand the panel to allow data entry. Enter in an account name.
Pressing the "Confirm" button will add the entered Account.
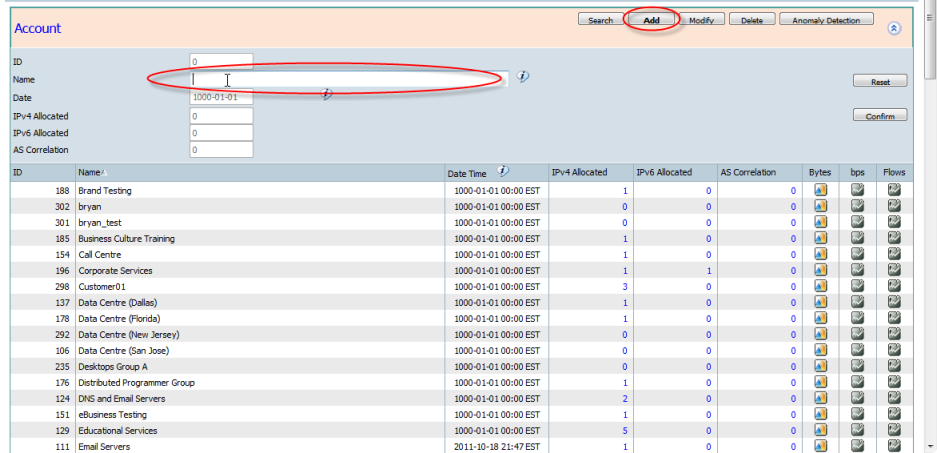
The Account ID is automatically generated.
- Modify - Highlight an Account using your mouse and then clicking the "Modify" button allows the selected Account Name to be edited.
Pressing the "Confirm" button will update the selected Account.
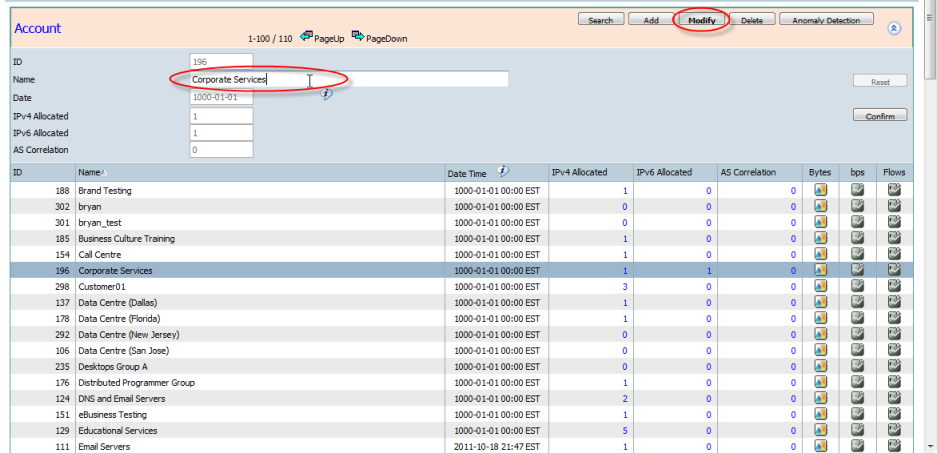
Only the account name can be changed.
- Delete - Highlight an Account using your mouse and then clicking the "Delete" button allows the selected Account Name to be Deleted.
Pressing the "Confirm" button will Delete the selected Account.
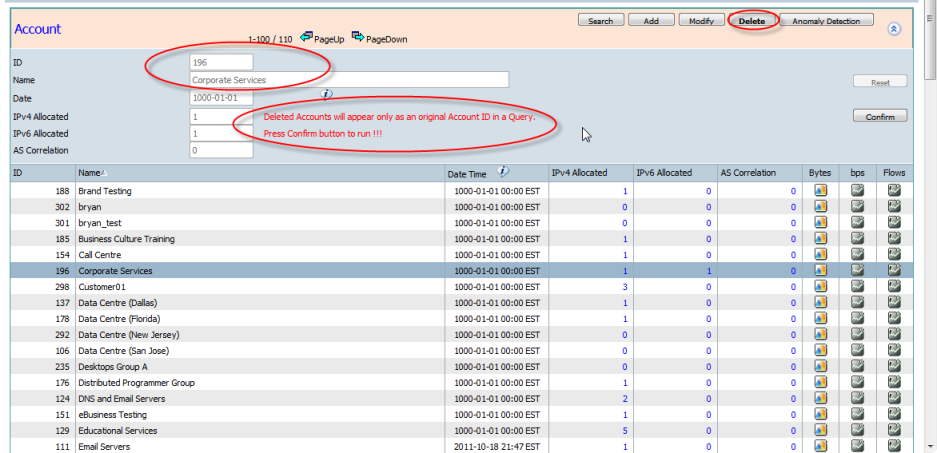
Accounts that have an Account id less than 10, are not allowed to removed.
A Deleted Account will appear as an Account id in a query or report if tagged traffic data already exists for the deleted account.
- Anomaly Detection - Highlight an Account using your mouse and then clicking the "Anomaly Detection" button allows the selected Account Name to begin generating a Baseline Alert for the highlighted Account.
Pressing the "Confirm" button will Enter the Forensics Template / Report / Alert Screen from where a simple "SaveNew" is all thats needed for CySight to begin learning and alerting Intelligent Baselines. See Forensics: 7. Creating Anomaly Detection Baseline Alerts and Forensics: 6. NBAD - Anomaly Detection Baseline Alerting.
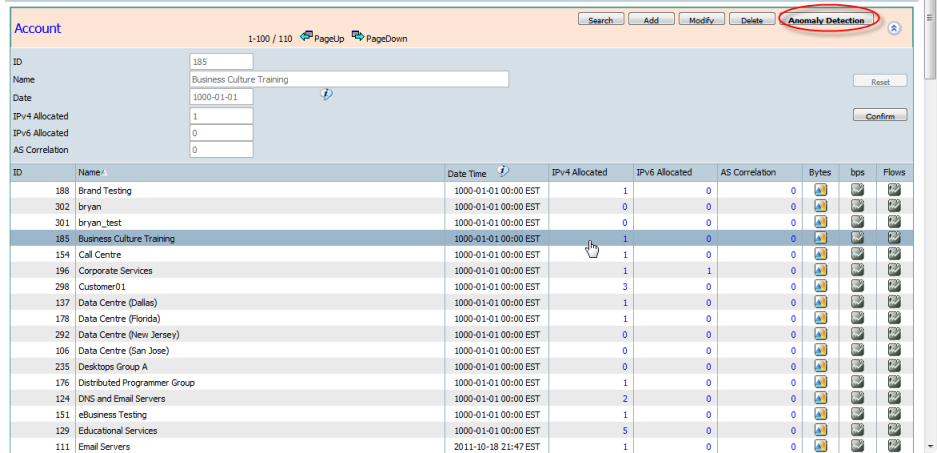

Too many baseline alerts could theoretically eventually impact netflow data collection or the systems ability to respond. If impact of collection does occur then CySight can be run in a Clustered Collection architecture
Clicking on the "IPv4 Allocated", "IPv6 Allocated" or "AS Correlation" values allows drill down to the respective "IPv4 Allocation", "IPv6 Allocation" or "Autonomous System" screens with the corresponding Account as the criteria.
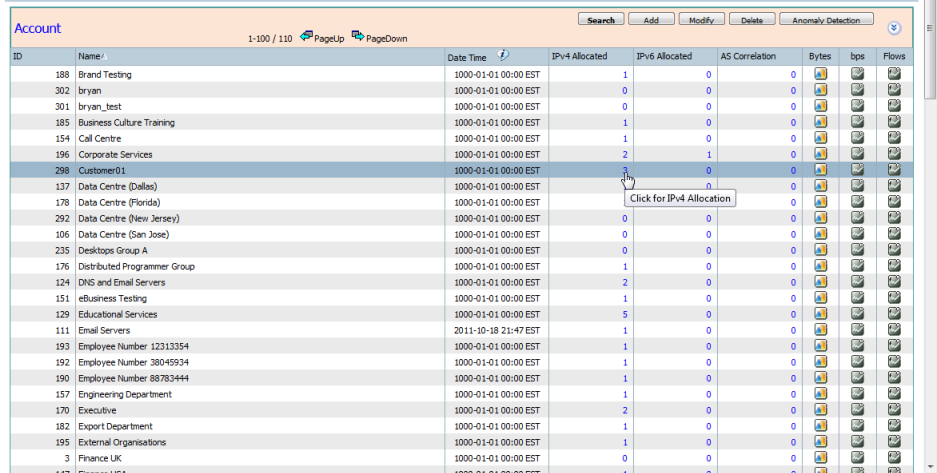
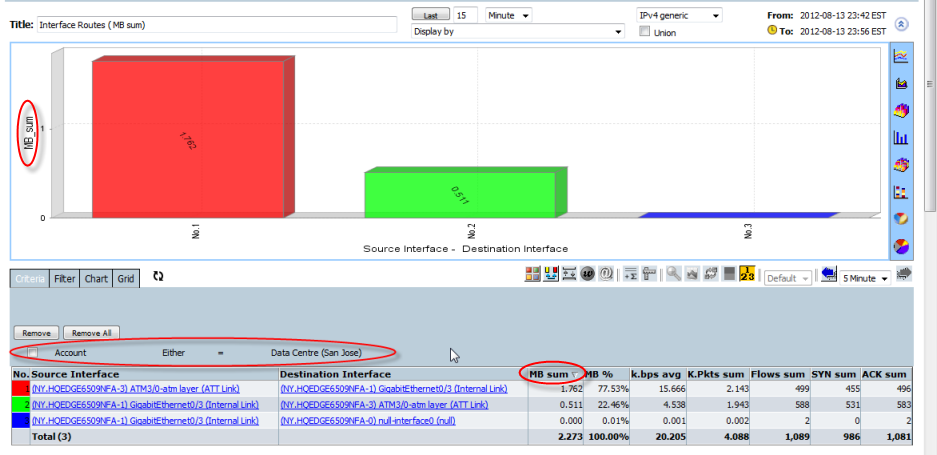
Clicking on the icons in the right columns allows drill down to an Interface Route view of the forensics screen with the corresponding Account as EITHER the Source account or the Destination Account as the Criteria.