An Easy Place to Start
The easiest way to filter traffic in CySight to identify likely P2P traffic is by going straight to the Top Talkers links in the CySight Real-Time menu.
In the CySight Real-Time menu click Real-Time/Flows/Business Groups/IP Address/Top Talkers D-S for the top talking IP addresses by source to destination. A chart similar to the following screen is then displayed.
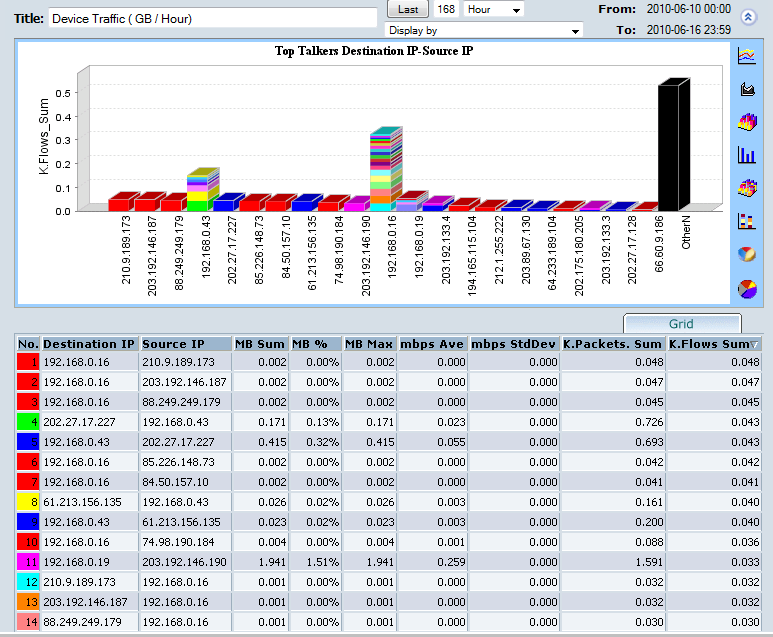
We can learn from this chart almost immediately that the IP Addresses 192.168.0.16 and 192.168.0.43 are obviously displaying some unusual traffic patterns. What is more is 192.168.0.16 is showing lots of different source ip addresses of small data chunks which would further raise the suspicions of P2P traffic on the network. To further analysze the traffic from 192.168.0.16 we could use the CySight drill down or filter aspects to analyze port informaton.
Filter the Report
If however this sort of traffic was not so noticable particularly in larger networks the CySight administrator may wish to further refine the report to beng the P2P traffic patterns to the surface. To this you need to go to the filter screen.
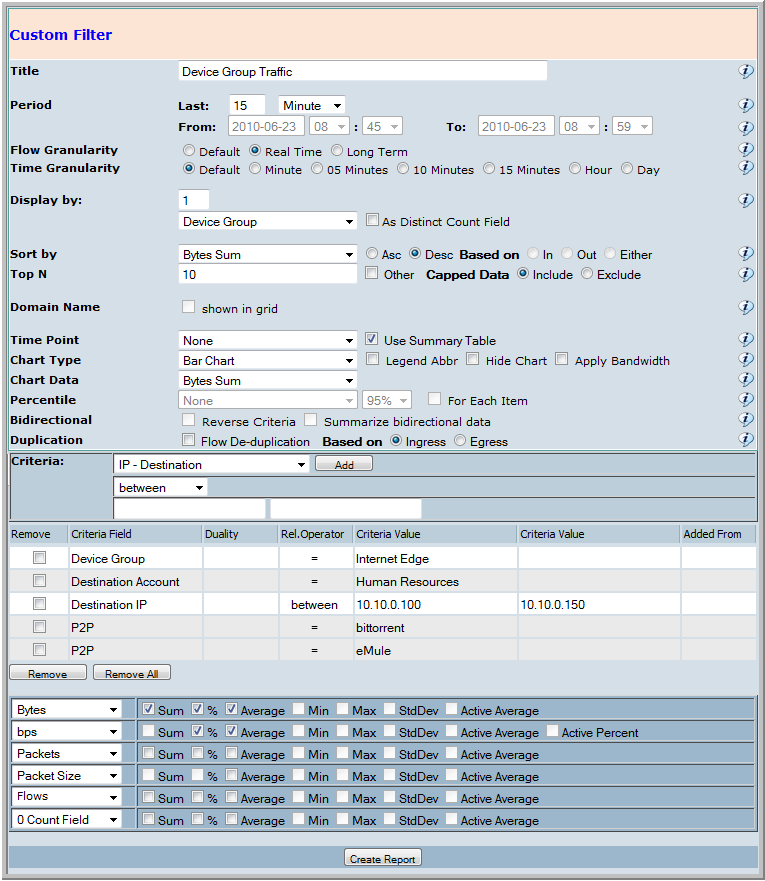
The first thing to do is uncheck 'Other' in the Top N line. This will remove the rollup of traffic outside the top number of IP addresses selected (default 50).
Next you may choose to exclude some known port numbers from your report to filter our email traffic on port 25 or ftp traffic on ports 20 & 21. If you have specialist applications you may wish to exclude port numbers for those applications, or microsoft application etc. etc... A word of warning, although most P2P traffic is conducted on unknown port numbers they can run on known ports also.
Next you may wish to confine your report to identify local source IP addresses only, such as 192.168.0.1-192.168.0.255 private IP range. This would limit the report to identifying the upload aspect of P2P which in many environments is easier to identify.
Finally you can then exclude the unlikely IP addresses such as servers.
Once this is done click create report.
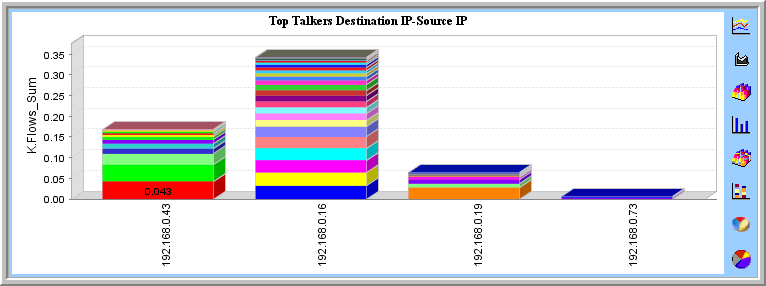
Identify the IP Address and Investigate
Once you have your results you will still need to investigate the machine for applications such as emule, bittorrent, uttorrent, warez etc.. However CySight should make this task a whole lot easier.
Save your Report
After all the filtering be sure to save your report as a template by clicking 'Save'. You can also schedule this report to run on a regular basis such as weekly or monthly.