At CySight, we recognize the critical importance of security in network management. That's why our solution incorporates robust features to leverage MAC addressing for enhanced security.
CySight's comprehensive correlation engine excels at identifying devices' Organizational Unique Identifier (OUI). The OUI represents the first 24 bits of a MAC address and indicates the specific vendor for that device. By leveraging this information, CySight enhances network security by enabling organizations to precisely identify and monitor authorized devices.
While MAC address analytics have raised privacy concerns in certain contexts, CySight takes security seriously. Our solution is designed to protect user privacy and ensure compliance with relevant regulations. We understand that tracking and privacy are valid concerns, and our focus is on providing a secure and trusted network environment.
In addition to MAC addressing, CySight offers a range of advanced security features to safeguard your network. We employ state-of-the-art encryption algorithms, robust authentication mechanisms, and intrusion detection capabilities. Our solution empowers organizations to implement granular access controls, monitor network behavior in real-time, and detect abnormal traffic flows.
We understand the challenges posed by dynamic MAC addressing and the need for network lockdown in certain environments. CySight provides flexible configuration options to adapt to evolving security requirements. Our expert team is always available to help you navigate the complexities of securing your network, ensuring that your organization can benefit from the advantages of MAC addressing while maintaining a strong security posture.
With CySight, you can confidently embrace MAC addressing as part of your security strategy, knowing that our solution prioritizes both network protection and user privacy. Partner with us and experience the peace of mind that comes with a robust and secure network management solution.
There is a time delay to show the MAC address information the first time it is included in the flow template for a Device. The MAC Address will begin displaying from the start of the next hour.The CySight MAC address left menu options. The MAC Address left menu options will begin displaying from the start of the next hour from the introduction of MAC address as a flow field.
The display by and criteria fields in the Custom Filter screens will display after any device is found to include the MAC address as one of the fields in the flow template.
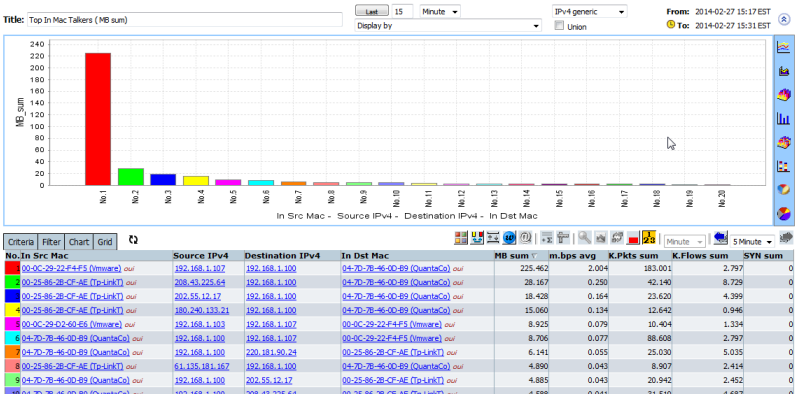
MAC Address is also used with Cisco WLC to identify both Station ID's and Device ID's.
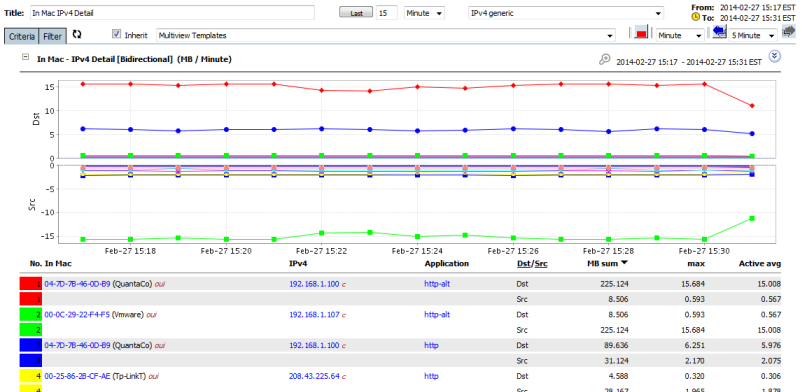
The Right click menu will also include the MAC address default menu's
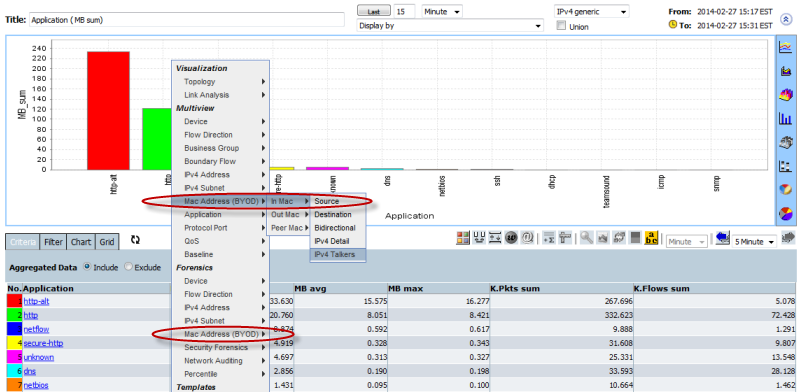
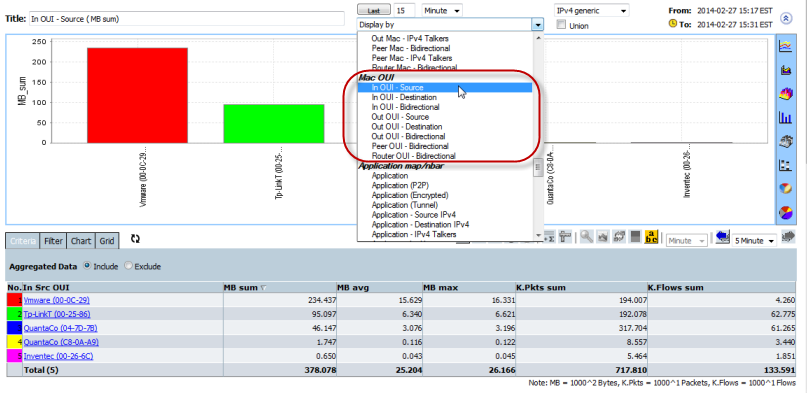
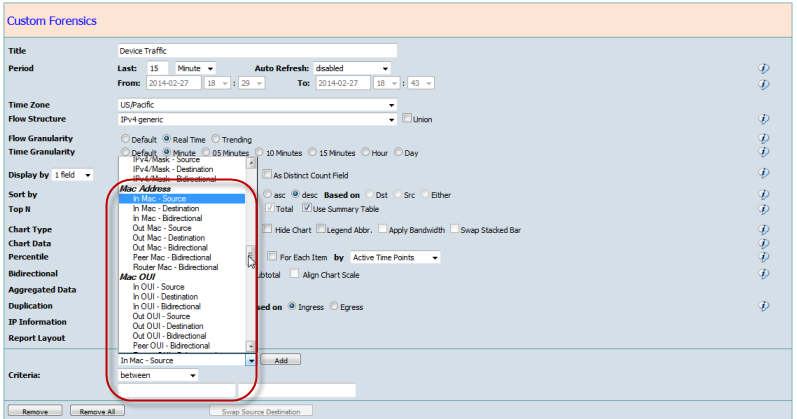
MAC Addresses can be used in the same way as any other data in CySight and can be included into Criteria. MAC Addresses can appear in the Display of Forensics or as part of Alerts criteria or have Counts applied to it .
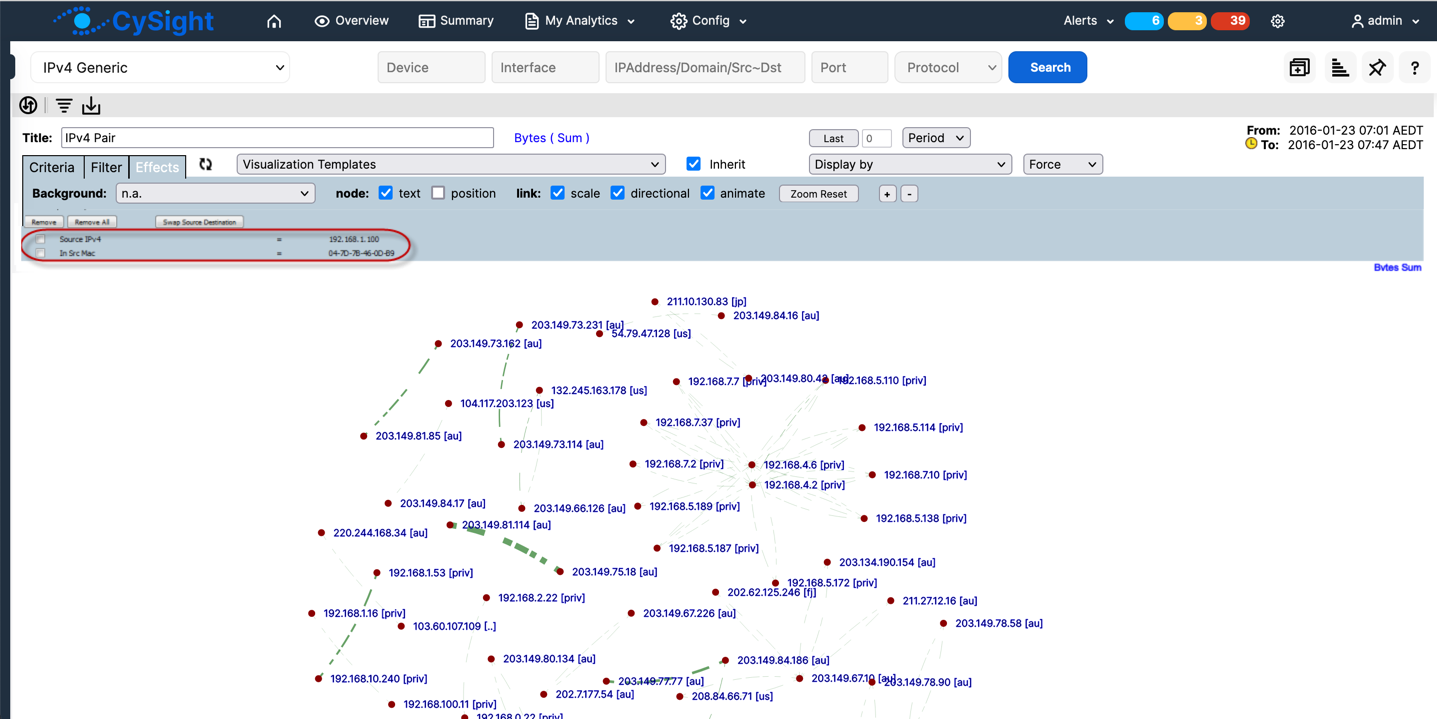
CySight's analysis of devices such as Cisco WLC employ the use of XY Analytics to provide cross sectional analysis e.g find all IP Addresses that have been used by a specified MAC address over the last month.
References
https://en.wikipedia.org/wiki/MAC_address
https://www.cisco.com/en/US/docs/net_mg ... #wp1017547
https://en.m.wikipedia.org/wiki/MAC_Table
https://www.techtimes.com/articles/8233 ... keters.htm
https://hal.archives-ouvertes.fr/file/i ... alking.pdf